What's new in Cogent: Multi-tier system ownership. Read about it here
Connect & normalize
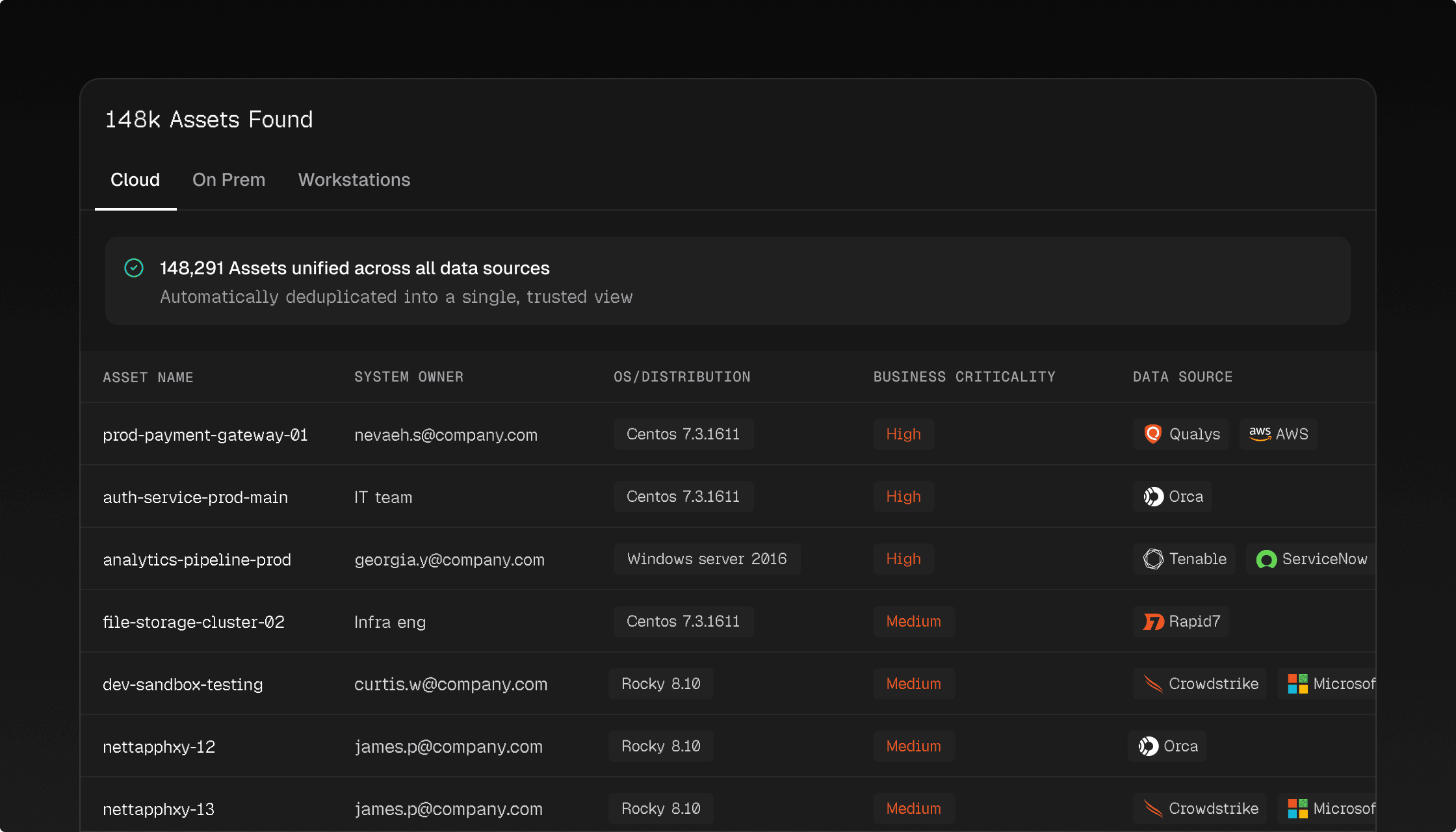
Start with data you can trust
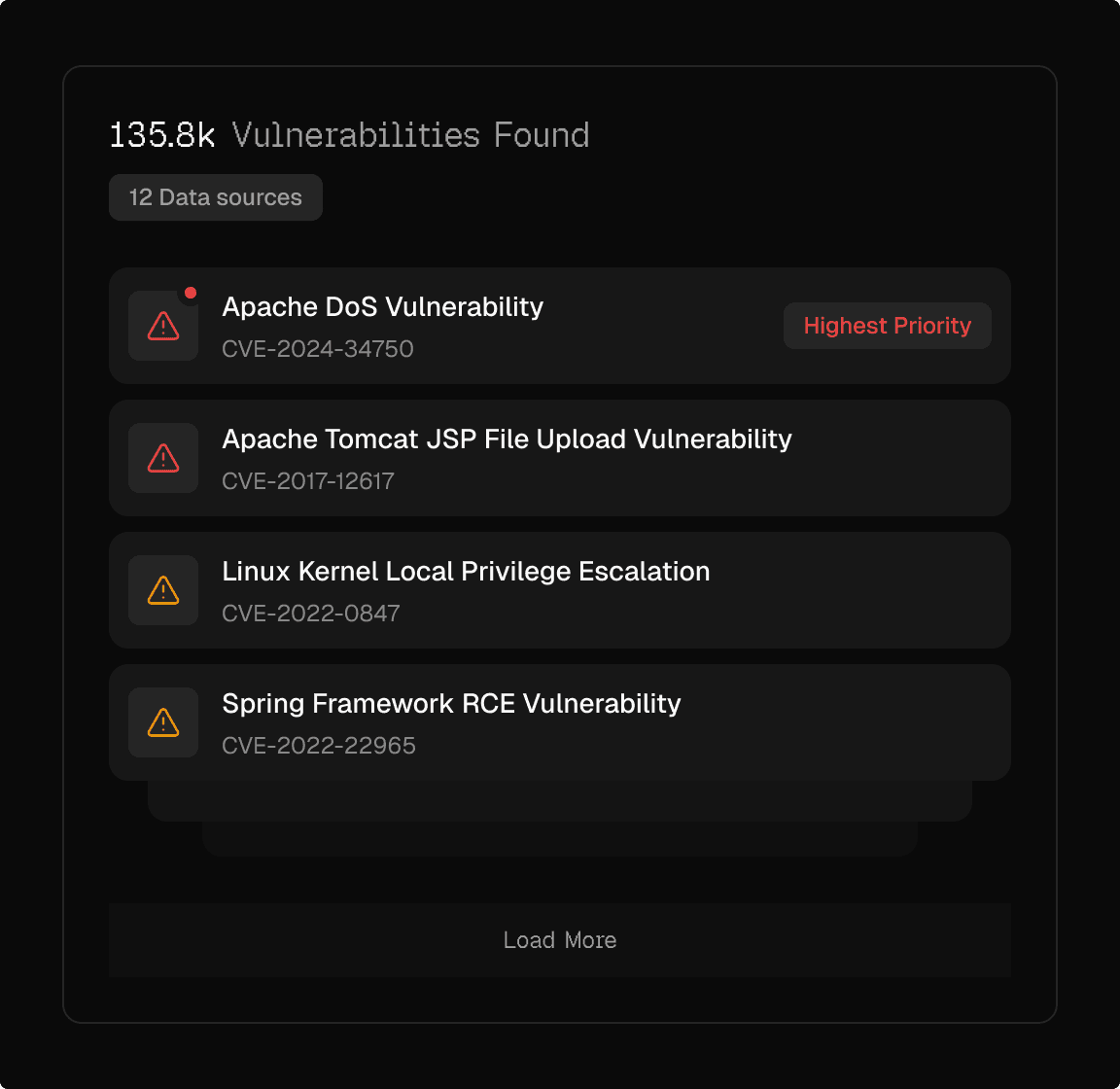
Cogent integrates with your existing security tools, deduplicates conflicting findings, and builds a unified knowledge base that shows what's actually exposed.
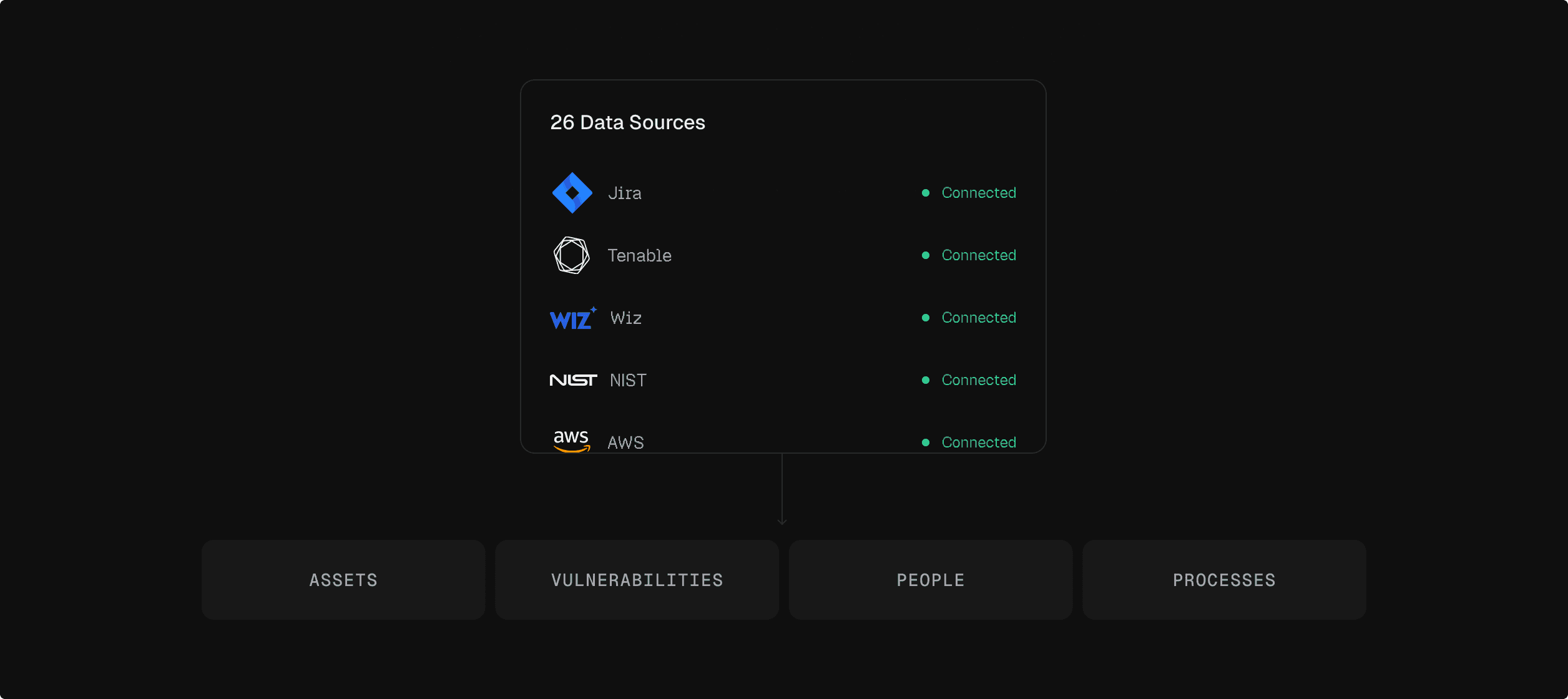
Connects to your entire stack
You don’t deploy Cogent, you connect it. Within minutes, Cogent begins building a picture of your assets and risk.
1
API-based integration
Connect all data sources via API. No agents to deploy, no scanner replacement required.
2
Security and business context sources
Ingest from vulnerability scanners, security tools, asset databases, and business applications.
3
Continuous sync and freshness
Configurable sync schedules keep data current and risk profiles accurate.
Builds a unified, trustworthy view
Cogent is a control plane across your security stack and it’s built on the foundation of a “single pane of glass” view of your environment.
1
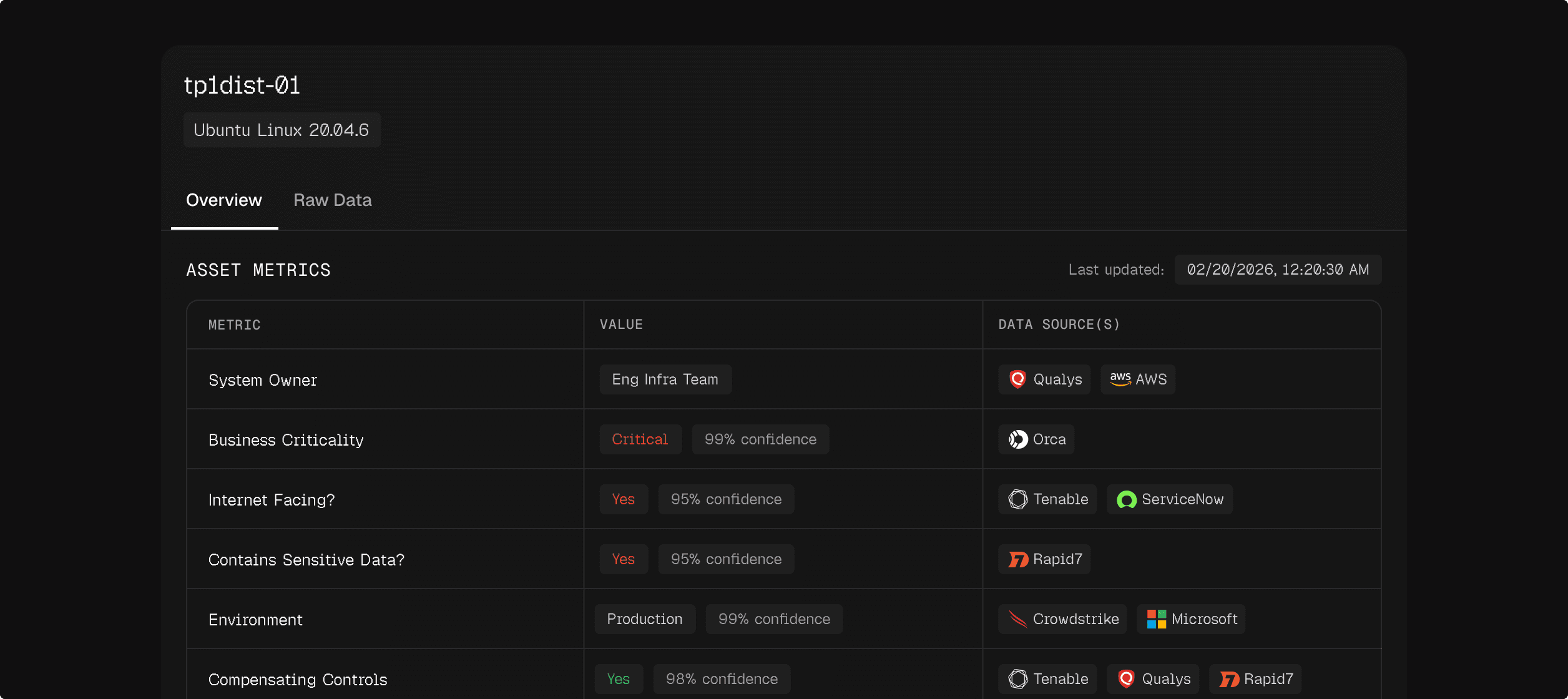
Cross-tool deduplication
When multiple scanners report the same vulnerability, Cogent consolidates them into a single record while preserving full provenance showing which tools observed it.
2
Confidence scoring on every attribute
See how certain Cogent’s AI agents are about every judgment. Drill into confidence breakdowns to understand which sources contributed and the corresponding reasoning.
3
Raw and aggregated views
Shows both the unified finding and the source-specific details from each tool.
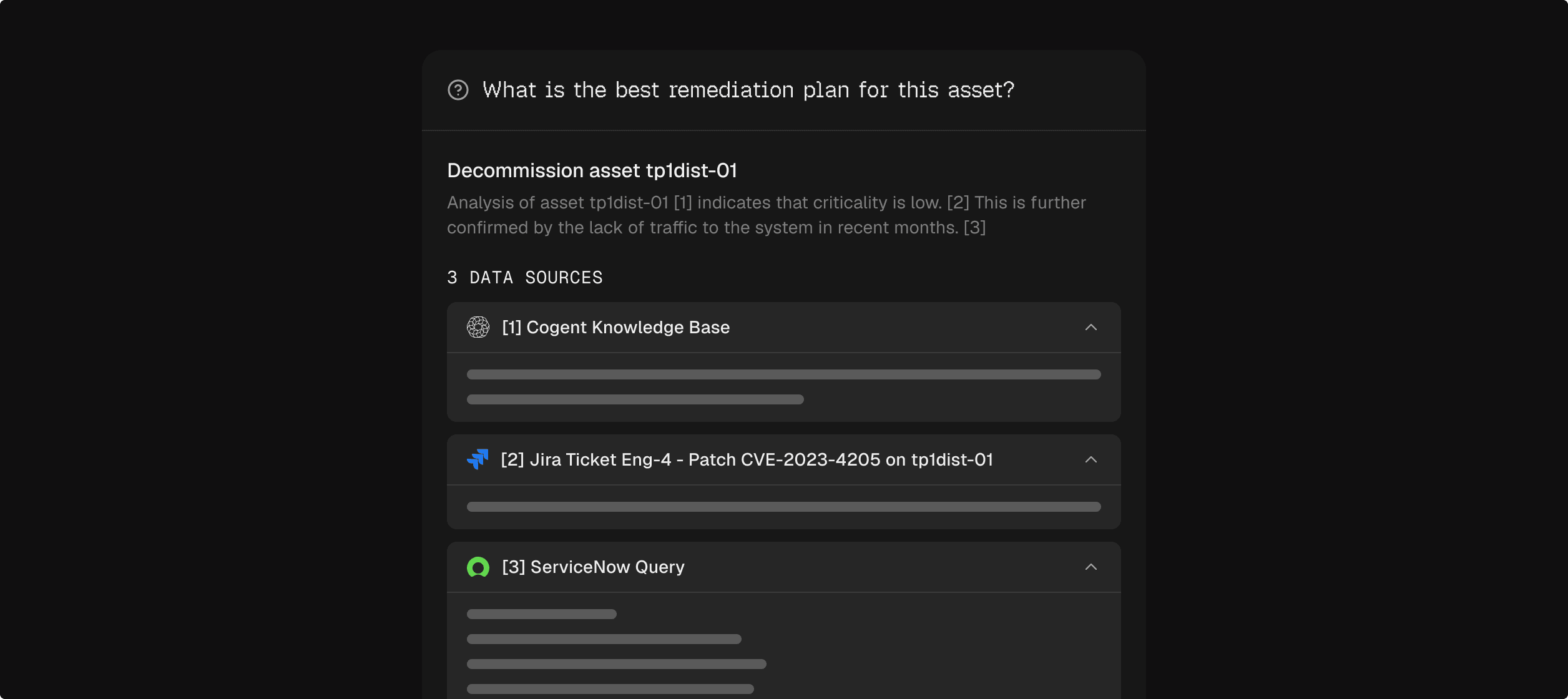
Understands how your teams actually work
Leverages deep business context to enable Cogent to drive remediation accurately and efficiently.
1
Ingests messy, unstructured data
Pulls in data sources from across the enterprise without requiring clean schemas.
2
Captures business requirements
Consolidates SLAs, risk acceptance policies, compliance requirements, and standard operating procedures.
3
Respects operational constraints
Understands team-specific patching workflows and availability concerns. Grounds remediation plans in reality, not theory.